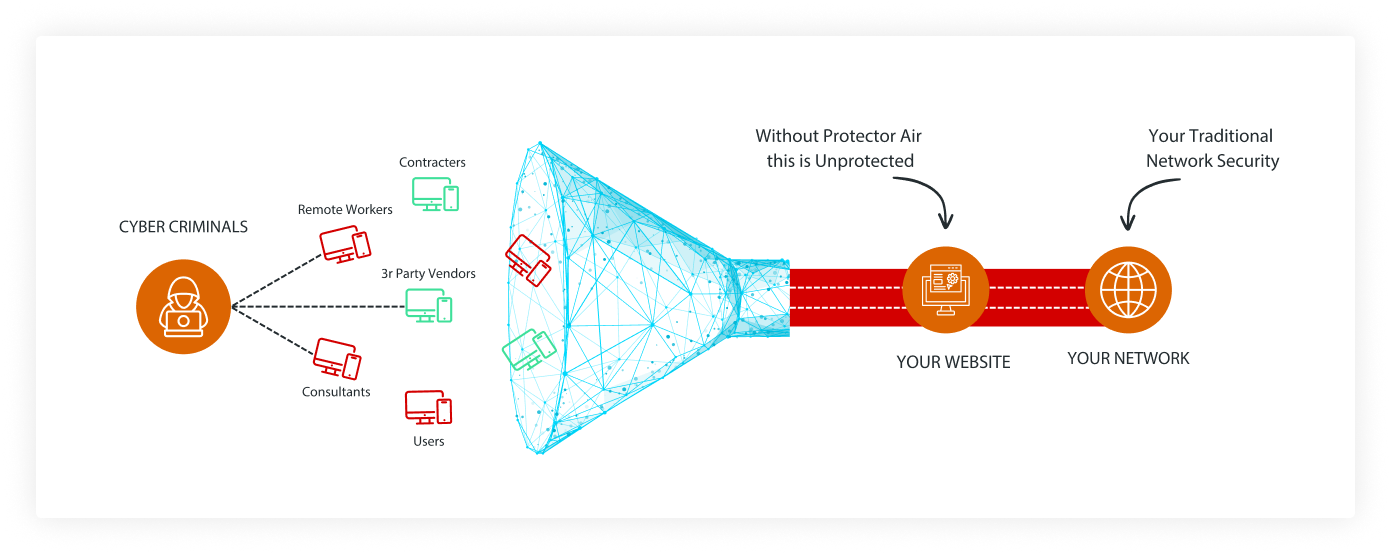
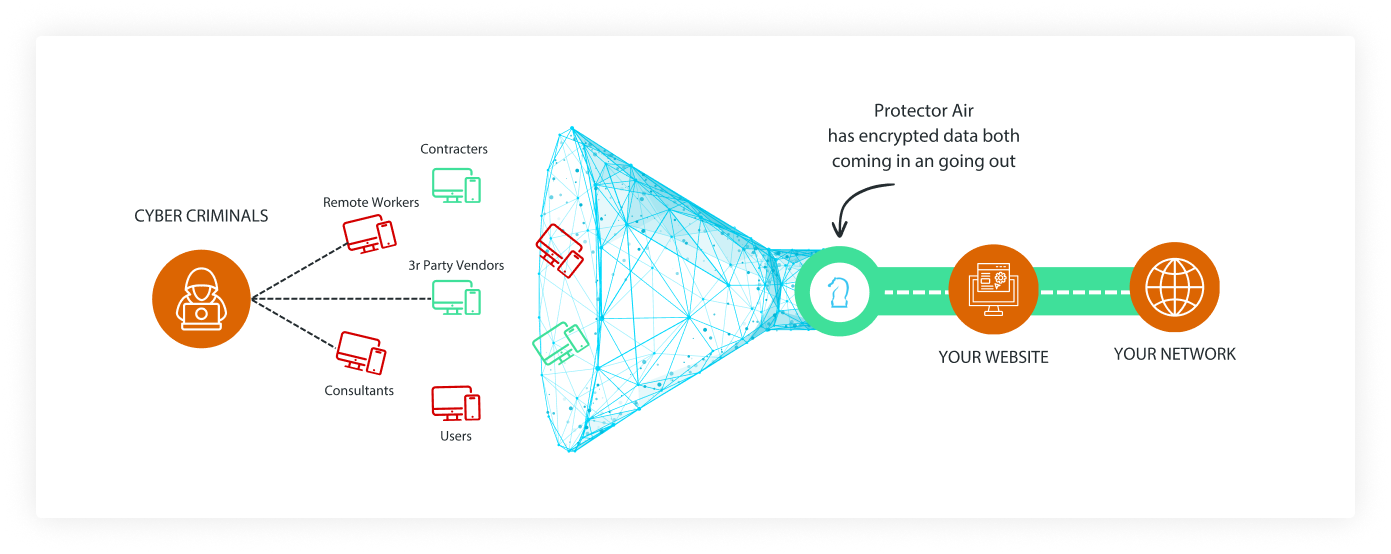
Trusted Knight Corporation or we provides this Privacy Policy to help you understand the types of information that you provide to what we do with that information and how we protect that information when you use Trusted Knight products and services.
Description of the Product/Service
With products and services, you can increase the protection for your digital data from hackers, spammers, spyware, malware and other online threats. Because of the fast and constantly evolving nature of online threats and malware, it is necessary to configure our products and services to occasionally provide data and information from your devices to enable us to stay ahead of malicious activities and protect your devices and data. This data and information can also include limited personal data.
Product license data
When you install and activate our products, you we may ask you toprovide personal data such as your:
- Name
- Phone number
- Email address
- Device ID
- Operating system
- License key
We use this personal data to ensure that your license to our solutions is valid and to contact you regarding renewals, technical issues and new product information.
Information and personal data for using and interacting with Trusted Knight products and services
We may ask you toprovide the following types of information and personal data when you use and interact with our products and services, including customer support. The specific information and personal data that you provide will depend on the particular product or services used. Providing these types of information and personal data enables you to participate, share and leverage Trusted Knight's global database of threat related intelligence to rapidly identify and defend against potential threats within your unique network environment, as described in more detail below as well as enabling us to provide support that you request.
- Product information, such as MAC address, device ID
- Public IP address of the user's gateway to the Internet
- Operating System version and security details
- Metadata from suspicious executable files
- Detected malicious file information
- Detected malicious network connection information
- Debug Logs
- Screen capture of errors
How does Trusted Knight use the data that you provide to us?
Our products use the personal data that you provide to perform security and threat detection related services and functions such as:
- Protection from malware such as keyloggers and, banking trojans.
- Threat prevention
- Identify sources and methods of targeted attacks.
- Deliver updated protection against new malicious threats
We may use information that you provide to us for other business purposes, including.
Internal record keeping.
Compliance with the law and requests from government bodies.
Product and service development.
Keeping you informed about our products, services and promotions.
Providing customer support, managinge subscriptions, and responding to requests, questions, and comments.
All the personal data stated above are necessary to enter into the contract with products and services.otherwise, we can information to perform our obligations to you.
How do we protect your information?
We use administrative, organizational, technical, and physical safeguards, including access controls, premises security measures, secure data destruction and incident response plans to protect the information that you provide to us. Our security controls are designed to maintain an appropriate level of data confidentiality, integrity, and availability.
Where do we process your data?
We may process your personal data at data centers in the United States as well as other locations around the world operated by Trusted Knight, affiliates of Trend MicrTrusted Knighto or data processors engaged by Trusted Knight who carry out data processing on behalf of Trusted Knight.
Data retention
We will keep information that you provide to us for as long as you are a registered subscriber or user of our products or for as long as we have another business purpose to do so and, thereafter, for no longer than is required or permitted by law.
How do we share your data?
We do not share data that you provide to us, except with service providers that help us perform and improve services for you, as necessary to perform our contractual obligations to you; in order to protect your, our and others' rights and interests; in connection with a sale or reorganization of our business, if and to the extent permissible by law and as required to cooperate with any legal process and any law enforcement or other government inquiry. This means that we may provide information that we collect from you if that information is relevant to a court subpoena or to a law enforcement authority or other government investigation, provided this is permissible under applicable data protection law.
Changes to the Trusted Knight Privacy Policy
This Privacy Policy was last updated in August 2018. Trusted Knight will occasionally update this Privacy Policy to reflect changes in our products and services and customer feedback. When we make changes to the Privacy Policy, we will revise the date at the top of the Privacy Policy. If there are material changes to this Privacy Policy or in how Trusted Knight will use your personal information, Trusted Knight will notify you either by prominently posting a notice of such changes prior to implementing the change or by directly sending you a notification.
Trusted Knight contact information and inquiries
If you have any questions, requests, comments or concerns regarding this Privacy Policy, please email us at help@trustedknight.com